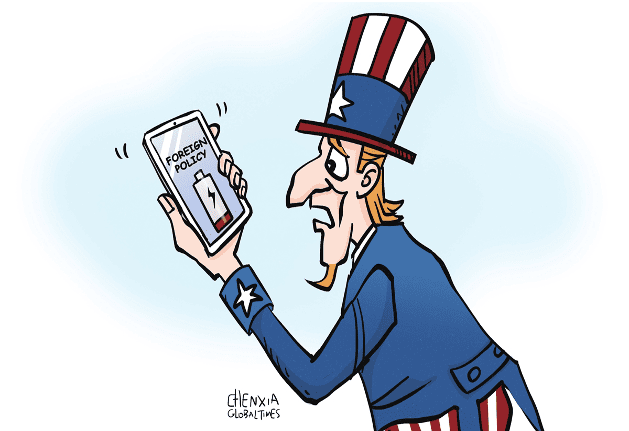
US foreign policy is advanced smartphone with weak battery
A couple of days ago, a Quad summit meeting in Sydney scheduled for May 24 was abruptly canceled. The US president had to pull out of his long-anticipated trip to Australia and Papua New Guinea. Instead, the heads of the four Quad member states got together on the margins of the G7 Summit in Hiroshima on May 20. The main reason for the change of plans was the continuous struggle between the White House and Republicans on the Hill over the national debt ceiling. If no compromise is reached, the US federal government might fail to meet its financial commitments already in June; such a technical default would have multiple negative repercussions for the US, as well as for the global economy and finance at large. Let us hope that a compromise between the two branches of US power will be found and that the ceiling of the national debt will be raised once again. However, this rather awkward last-minute cancellation of the Quad summit reflects a fundamental US problem - a growing imbalance between the US geopolitical ambitions and the fragility of the national financial foundation to serve these ambitions. The Biden administration appears to be fully committed to bringing humankind back to the unipolar world that existed right after the end of the Cold War some 30 years ago, but the White House no longer has enough resources at its disposal to sustain such an undertaking. As they say in America: You cannot not have champagne on a beer budget. The growing gap between the ends that the US seeks in international relations and the means that it has available is particularly striking in the case of the so-called dual containment policy that Washington now pursues toward Russia and China. Even half a century ago, when the US was much stronger in relative terms than it is today, the Nixon administration realized that containing both Moscow and Beijing simultaneously was not a good idea: "Dual containment" would imply prohibitively high economic costs for the US and would result in too many unpredictable political risks. The Nixon administration decided to focus on containing the Soviet Union as the most important US strategic adversary of the time. This is why Henry Kissinger flew to Beijing in July 1971 to arrange the first US-China summit in February 1972 leading to a subsequent rapid rapprochement between the two nations. In the early days of the Biden administration, it seemed that the White House was once again trying to avoid the unattractive "dual containment" option. The White House rushed to extend the New START in January 2021 and held an early US-Russia summit meeting five months later in Geneva. At that point many analysts predicted that Biden would play Henry Kissinger in reverse - that is he would try to peace with the relatively weaker opponent (Moscow) in order to focus on containing the stronger one (Beijing). However, after the beginning of the Russia-Ukraine conflict, it became clear that no accommodation with the Kremlin was on Biden's mind any longer. Still, having decided to take a hard-line stance toward Moscow and to lead a broad Western coalition in providing military and economic assistance to Kiev, Washington has not opted for a more accommodative or at least a more flexible policy toward Beijing. On the contrary, over last year one could observe a continuous hardening of the US' China policy - including granting more political and military support to the Taiwan island, encouraging US allies and partners in Asia to increase their defense spending, engaging in more navel activities in the Pacific and imposing more technology sanctions on China. In the meantime, economic and social problems within the US are mounting. The national debt ceiling is only the tip of an iceberg - the future of the American economy is now clouded by high US Federal Reserve interest rates that slow down growth, feed unemployment and might well lead to a recession. Moreover, the US society remains split along the same lines it was during the presidency of Donald Trump. The Biden administration has clearly failed to reunite America: Many of the social, political, regional, ethnic and even generational divisions have got only deeper since January 2021. It is hard to imagine how a nation divided so deeply and along so many lines could demonstrate continuity and strategic vision in its foreign policy, or to allocate financial resources needed to sustain a visionary and consistent global leadership. Of course, the "dual containment" policy is not the only illustration of the gap between the US ambitions and its resources. The same gap inevitably pops up at every major forum that the US conducts with select groups of countries from the Global South - Africa, Southeast Asia, Latin America or the Middle East. The Biden administration has no shortage of arguments warning these countries about potential perils of cooperating with Moscow or Beijing, but it does not offer too many plausible alternatives that would showcase the US generosity, its strategic vision, and its true commitment to the burning needs of the US interlocutors. To cut it short, Uncle Sam brings lots of sticks to such meetings, but not enough carrots to win the audience. In sum, US foreign policy under President Joe Biden reminds people of a very advanced and highly sophisticated smartphone that has a rather weak battery, which is not really energy efficient. The proud owner of the gadget has to look perennially for a power socket in order not to have the phone running out of power at any inappropriate moment. Maybe the time has come for the smartphone owner to look for another model that would have fewer fancy apps, but a stronger and a more efficient battery, which will make the appliance more convenient and reliable.

See Pregnant Margot Robbie Debut Her Baby Bump
This Barbie is going to be a mother. And Margot Robbie has no problem putting her burgeoning baby bump on full display. In fact, the Barbie star, who is pregnant with her Tom Ackerley’s first baby, debuted recently her bump while vacationing on Italy’s Lake Como with her husband July 7. For the outing, Margot donned a black blazer over a white tee that was cropped above her stomach, showing off a sweet baby bump. She finished off the look with low-rise black trousers, black platform sandals and a summery straw bag. For his part, Tom—whom Margot wed in a 2016 ceremony in her native Australia—wore olive green trousers and a cream-colored button-down shirt and tan sneakers. The couple were photographed waiting on a dock in Lake Como before they hopped in a boat and sailed off into a literal sunset. While Margot and Tom, both 34, haven’t spoken publicly about their upcoming bundle of joy, the I, Tonya alum has previously expressed hope to have a big family one day. As she told Porter in 2018, “If I'm looking into my future 30 years from now, I want to see a big Christmas dinner with tons of kids there.” Tom and Margot’s new chapter comes over ten years after their love story first began on the set of 2014's Suite Française, in which Margot starred while Tom worked as a third assistant director. But while she was immediately smitten, Margot was convinced her love would go unrequited. "I was always in love with him, but I thought, ‘Oh, he would never love me back,'" she admitted to Vogue in 2016. "'Don't make it weird, Margot. Don't be stupid and tell him that you like him.' And then it happened, and I was like, ‘Of course we're together. This makes so much sense, the way nothing has ever made sense before.'"

Israeli strike kills a senior Hezbollah commander in south Lebanon
BEIRUT/JERUSALEM July 3 (Reuters) - An Israeli strike killed one of Hezbollah's top commanders in south Lebanon on Wednesday, prompting retaliatory rocket fire by the Iran-backed group into Israel as their dangerously poised conflict rumbled on. The Israeli military said it had struck and eliminated Hezbollah's Mohammed Nasser, calling him commander of a unit responsible for firing from southwestern Lebanon at Israel. Nasser, killed by an airstrike near the city of Tyre in southern Lebanon, was the one of the most senior Hezbollah commanders to die yet in the conflict, two security sources in Lebanon said. Sparked by the Gaza war, the hostilities have raised concerns about a wider and ruinous conflict between the heavily armed adversaries, prompting U.S. diplomatic efforts aimed at deescalation. Israeli Defence Minister Yoav Gallant said Israeli forces were hitting Hezbollah "very hard every day" and will be ready to take any action necessary against the group, though the preference is to reach a negotiated arrangement. Hezbollah began firing at Israeli targets at the border after its Palestinian ally Hamas launched the Oct. 7 attack on Israel, declaring support for the Palestinians and saying it would cease fire when Israel stops its Gaza offensive. Hezbollah announced at least two attacks in response to what it called "the assassination", saying it launched 100 Katyusha rockets at an Israeli military base and its Iranian-made Falaq missiles at another base in the town of Kiryat Shmona near the Israeli-Lebanese border. Israel's Channel 12 broadcaster reported that dozens of rockets were fired into northern Israel from Lebanon. There were no reports of casualties. The Israeli Defence Ministry said that air raid sirens sounded in several parts of northern Israel. Israel's military did not give a number of rockets launched but said most of them fell in open areas, some were intercepted, while a number of launches fell in the area of Kiryat Shmona.

Morning Bid: Eyes switch to inflation vs elections, Powell up
A look at the day ahead in U.S. and global markets from Mike Dolan After an intense month focused on election risk around the world, markets quickly switched back to the more prosaic matter of the cost of money - and whether disinflation is resuming to the extent it allows borrowing costs to finally fall. Thursday's U.S. consumer price update for June is the key moment of the week for many investors - with the headline rate expected to have fallen two tenths of a percentage point to 3.1% but with 'core' rates still stuck at 3.4%. With Federal Reserve chair Jerome Powell starting his two-pronged semi-annual congressional testimony later on Tuesday, the consensus CPI forecast probably reflects what the central bank thinks of the situation right now - encouraging but not there yet. But as the U.S. unemployment rate is now back above 4.0% for the first time since late 2021, markets may look for a more nuanced approach from the Fed chair that sees it increasingly wary of a sudden weakening of the labor market as real time quarterly GDP estimates ebb again to about 1.5%. There were some other reasons for Fed optimism in the lead up to the testimony. The path U.S. inflation is expected to follow over coming years generally softened in June, amid retreating projections of price increases for a wide array of consumer goods and services, a New York Fed survey showed on Monday. Inflation a year from now was seen at 3% as of June - down from the expected rise of 3.2% in May - and five-year expectations fell to 2.8% from 3%. Crude oil prices are better behaved this week, too, falling more than 3% from the 10-week highs hit late last week and halving the annual oil price gain to 10%. The losses on Tuesday came after a hurricane that hit a key U.S. oil-producing hub in Texas caused less damage than many in markets had expected - easing concerns over supply disruption. Before Powell starts speaking later, there will also be an update on U.S. small business confidence for last month.

Portadown businessman avoids jail for sexual assault of teen under his employment
Defence said the defendant 'continues to deny' the charges and bail in the sum of £1,000 was fixed for appeal
A Portadown man has avoided jail after sexually assaulting a 16-year-old shop worker under his employment. -ADVERTISEMENT- Brian Thomas Chapman (58), of Moyallan Road, appeared before Newry Magistrates’ Court on Monday for sentencing on two counts of sexual assault. The prosecution outlined that on September 23, 2020, a 16-year-old student in the employment of Brian Chapman, disclosed to her mother about incidents that had occurred in her workplace. She said Chapman had put his hand on her thigh and the back of her leg. She also disclosed that she had been getting extra money from him and he had been sending her text messages. The allegations were reported to police the next day, September 24. The victim then took part in an interview on October 9, in which she said, when she was alone in Chapman’s office, he placed his hand on her upper thigh and his other hand on her lower back, underneath her trousers. The defendant was arrested and interviewed at Lurgan police station, where he denied the allegations. His phone was seized and an examination was carried out. The first interview of the defendant took place on October 9, during which he admitted to sending a message about wanting the victim to work 24/7, but stated this was a joke. The second interview took place on January 28, 2021, where he admitted to sending the 24/7 message, but denied sending other messages, such as “hope you’re spending the pounds on something special”. Throughout this process, Chapman denied sending the messages and denied any of the sexual assaults alleged by the victim. On the Chapman’s criminal record, the prosecution added that he was convicted of three common assaults on appeal. In terms of commission, these matters pre-dated this case but the conviction occurred during the running of this case and also involved a female working for the defendant. Prosecution continued that the age of the victim was an aggravating feature, arguing there was a “vulnerability” due to the “power-imbalance” between Chapman and the young student working for him. An additional aggravating feature, they said, was that during the course of the defence, part of the defence was that the victim had “manipulated or manufactured” some of the text messages that were sent. A defence lawyer, speaking on the pre-sentence report, noted the author deemed Chapman to be of low risk. He also noted that similar offences were contested in the County Court in respect of another complaint, with the judge substituting indecent assault charges for common assault. He also argued a Sexual Offences Prevention Order (SOPO) was not necessary as the offending was four years ago, there has been no repetition and risk had been addressed. District Judge Eamonn King noted the defendant was convicted on two of four original charges following a contest, which ran over a number of days, with the case adjourned for a pre-sentence report and victim impact statement to be produced. He added the defendant “continues to deny” the charges and seeks to appeal the outcome. District Judge King, on reading the pre-sentence report, noted the defendant “denies ever hugging or touching the individual and he denies any sexual attraction to the victim”, but pointed to a paragraph in the report which stated, “From the available evidence, it’s possible to surmise that he demonstrated risk taking and impulsive behaviour. It appears that he took advantage of his position and power in a bid to meet his sexual needs, given the victim’s young age and the fact that he was her employer”. The report added that this demonstrated “limited victim empathy and responsibility due to his denial of the offences”. On the victim impact statement, District Judge King described her as a young girl getting her first job, with the “world as her oyster”. He continued: “As a result of what she says occurred, that turned on its head. It left her feeling inwardly uncomfortable, anxious and lonely. She cut herself off from her friends. She stopped going out. She didn’t want to go to school.” He also described a “degree of manipulation” in the case, as this was the victim’s first job and there was a power imbalance between her as an employee, and Chapman as the employer. In his sentencing remarks, District Judge King, said: “I’ve taken time to emphasise to the victim in this case that the victim did nothing wrong. The victim did everything right and the victim shouldn’t feel lonely, anxious or isolated. “The victim should feel confident, strong and outgoing.” Owing to the defendant’s ongoing denial of the charges, he added: “My sentencing exercise isn’t the conclusion of the case today, but I will sentence, so that we can move towards the conclusion going forward. “I am satisfied, irrespective of what the pre-sentence report says, that the defendant took advantage of someone, attempted to groom someone and was guilty of the two offences.” On the two counts, Chapman was sentenced to three months in prison, suspended for two years. He was also made subject to a Sexual Offences Prevention Order (SOPO) for five years and placed on the sex offenders’ register for seven years. Following sentencing, District Judge King fixed bail for appeal at £1,000.





