Beyond the aurorae: How solar flares spill out across the Solar System
The Sun is extremely active right now, blasting the Earth with the biggest solar storms in 20 years. This is what it is doing to the rest of the Solar System. If you happened to look skywards on a few nights in May 2024, there was a good chance of seeing something spectacular. For those at relatively low latitudes, there was a rare chance to see the flickering red, pink, green glow of our planet's aurorae. A powerful solar storm had sent bursts of charged particles barrelling towards Earth and, as they bounced around in our planet's atmosphere, they unleashed spectacular displays of the Northern and Southern Lights. The dazzling displays of aurora borealis were visible far further south than they might normally be – and far further north in the case of aurora australis thanks to the power of the geomagnetic storm, the strongest in two decades. Although some people experienced only a faint, eerie glow, others were treated to a myriad of colour as far south as London in the UK and Ohio in the US. Reports even came in from just to the north of San Francisco, California. But while this spike in activity from the Sun left many on Earth transfixed by the light display it produced, it has also had a profound effect elsewhere in the Solar System. As most of us wondered at the colours dancing across the night's sky, astronomers have been peering far beyond to see the strange ways such intense bursts of particles affect other planets and the space between them. "The Sun can fire material outwards in any direction like a garden sprinkler," says Jim Wild, a professor of space physics at Lancaster University in the UK. "The effects are felt throughout the Solar System." Our Sun is currently heading towards, or has already reached, its solar maximum – the point in an 11-year cycle where it is most active. This means the Sun produces more bursts of radiation and particles from solar flares and events known as coronal mass ejections (CMEs). If these are sprayed in our direction, they can supercharge the Earth's magnetic field, causing magnificent aurorae but also posing problems for satellites and power grids. "Things really seem to be picking up right now," says Mathew Owens, a space physicist at the University of Reading in the UK. "I think we're about at solar maximum now, so we may see more of these kinds of storms in the next couple of years." Around the Sun, multiple spacecraft are observing this increase in activity up close. One of those, the European Space Agency's (Esa) Solar Orbiter, has been studying the Sun since 2020 on an orbit that takes it within the path of Mercury. Currently the spacecraft is "on the far side of the Sun as seen from Earth", says Daniel Müller, project scientist for the Solar Orbiter mission at Esa in the Netherlands. "So we see everything that Earth doesn't see." The storm that hit Earth in May originated from an active region of solar flares and sunspots, bursts of plasma and twisting magnetic fields on the Sun's surface, known as its photosphere. Solar Orbiter was able to see "several of the flares from this monster active region that rotated out of Earth's view", says Müller, bright flashes of light and darkened regions called sunspots on the Sun's surface. One of the goals of Solar Orbiter is "to connect what's happening on the Sun to what's happening in the heliosphere," says Müller. The heliosphere is a vast bubble of plasma that envelops the Sun and the planets of the Solar System as it travels through interstellar space. What Müller and his colleagues hope to learn more about is where the solar wind – the constant stream of particles spilling out from the Sun across the Solar System – "blows into the interstellar medium", he says. "So we are particularly interested in anything energetic on the Sun that we can find back in the turbulence of the solar wind." This particular cycle, cycle 25, appears to be "significantly more active than what people predicted", says Müller, with the relative sunspot number – an index used to measure the activity across the visible surface of the Sun – eclipsing what was seen as the peak of the previous solar cycle. The National Oceanic and Atmospheric Administration (Noaa) in the US had predicted a maximum monthly average of 124 sunspots a day in May, but the actual number was 170 on average, with one day exceeding 240, according to Müller. But the exact cause of the Sun's 11-year-long cycle and its variabilities remains a bit of a mystery. • Alien aurora: The strange displays that light up other worlds • Why Einstein was wrong about black holes • The Moon is slipping away from the Earth – and our days are getting longer The effects of these changes in solar activity, however, extend far across the Solar System. Earth is not the only planet to be hit by solar storms as they billow across interplanetary space. Mercury, the closest planet to the Sun, has a much weaker magnetic field than Earth – about 100 times less – and lacks a substantial atmosphere. But solar activity can cause the surface of the planet to glow with X-rays as solar wind rains down. Venus also lacks a substantial magnetic field, but the planet does still create auroras as the solar wind interacts with the planet's ionosphere. At Mars, the effect of solar activity is more obvious. Here, a Nasa spacecraft called Maven (Mars Atmosphere and Volatile Evolution) has been studying the planet's atmosphere from orbit since 2014. "We were on the declining side of solar cycle 24 [then]," says Shannon Curry, a planetary scientist at the University of Colorado, Boulder in the US and the lead on the mission. "We are now coming up on the peak of cycle 25, and this latest series of active regions has produced the strongest activity Maven has ever seen." Between 14 and 20 May the spacecraft detected exceptionally powerful solar activity reaching Mars, including an X8.7 – solar flares are ranked B, C, M, and X in order from weakest to strongest. Results from the event have yet to be studied, but Curry noted that a previous X8.2 flare had resulted in "a dozen papers" published in scientific journals. Another flare on 20 May, later estimated to be an even bigger X12, hurled X-rays and gamma rays towards Mars before a subsequent coronal mass ejection launched a barrage of charged particles in the same direction. Images beamed back from Nasa's Curiosity Rover on Mars revealed just now much energy struck the Martian surface. Streaks and dots caused by charged particles hitting the camera's sensors caused the images to "dance with snow", according to a press release from Nasa. Maven, meanwhile, captured glowing aurora as the particles hit the Mars' atmosphere, engulfing the entire planet in an ultraviolet glow. The flares can cause the temperature of the Martian atmosphere to "dramatically increase," says Curry. "It can even double in the upper atmosphere. The atmosphere itself inflates. The entire atmosphere expands dozens of kilometres – exciting for scientists but detrimental for spacecraft, because when the atmosphere expands there's more drag on the spacecraft." The expanding atmosphere can also cause degradation of the solar panels on spacecraft orbiting Mars from the increase in radiation. "The last two flares caused more degradation than what a third of a year would typically do," says Curry. Mars, while it has lost most of its magnetic field, still has "crustal remnant magnetic fields, little bubbles all over the southern hemisphere", says Curry. During a solar event, charged particles can light those up and excite particles. "The entire day side lights up in what we call a diffuse aurora," says Curry. "The entire sky glows. This would most likely be visible to astronauts on the surface." By the time solar storms reach further out into the solar system, they tend to have dissipated but can still have an impact on the planets they encounter. Jupiter, Saturn, Uranus, and Neptune all have aurorae that are in part driven by charged particles from the Sun interacting with their magnetic fields. But one of the key effects of solar activity on interplanetary space that astronomers are eager to study is something called "slow solar wind", a more sluggish, but denser stream of charged particles and plasma from the Sun. Steph Yardley, a solar astronomer at Northumbria University in the UK, says solar wind is "generally classed about 500km/s (310 miles/s)", but slow wind falls below this. It also has a lower temperature and tends to be more volatile. Recent work by Yardley and her colleagues, using data from Solar Orbiter, suggests that the Sun's atmosphere, its corona, plays a role in the speed of the solar wind. Regions where the magnetic field lines, the direction of the field and charged particles are "open" – stretching out into space without looping back – provide a highway for solar wind to reach high speeds. Closed loops over some active regions – where the magnetic field lines have no beginning and end – can occasionally snap, producing slow solar wind. The variability in the slow solar wind seems to be driven by the unpredictable flow of plasma inside the Sun, which makes the magnetic field particularly chaotic. The X-class flares and coronal mass ejections seen in May transformed the interplanetary medium as they flung out material across the solar system. Solar Orbiter detected a huge spike in ions moving at thousands of kilometres per second immediately after the 20 May flare. Computers on board other spacecraft – the BepiColombo probe, which is currently on a seven-year journey to Mercury, and Mars Express, in orbit around the Red Planet – both saw a dramatic increase in the number of memory errors caused by the high energy solar particles hitting the memory cells. The day after the coronal mass ejection, magnetometers on board the Solar Orbiter also saw large swings in the magnetic field around the spacecraft as a huge bubble of plasma made up of charged particles thrown out from by the event washed past it at 1,400km/s (870 miles/s). Increased solar activity is a boon for scientists. "If you track the number of papers produced by solar physicists, you can almost see an 11-year cycle in there," says Owens. "We are all more scientifically productive when there's a lot of activity to study." As the Sun continues into solar maximum, the Solar System will see more and more activity streaming from its surface. Yet while all the planets witness at least some of the activity, our planet bears the brunt more than most. "Earth is slightly unique in that space weather can have interesting effects on human technologies," says Wild. "There's an extra dimension here on Earth." Perhaps one day those anthropogenic effects might be felt elsewhere, too. "If you're going to fly to Mars and you have a six-month flight through the interplanetary environment, you're going to potentially suck up a lot of space weather events," says Wild. "How you protect your astronauts is an interplanetary issue that we need to get our heads around."
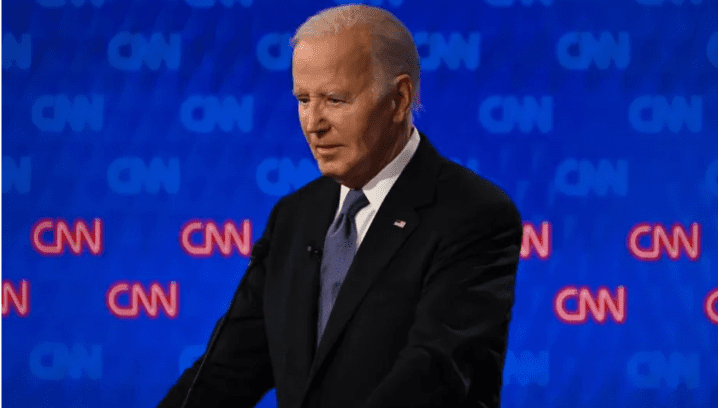
Biden accelerated aging over the past year!
n a recent interview with ABC, US President Joe Biden said he had no intention of dropping out of the race, blaming his poor debate performance on a cold. He also insisted he was "still in good shape" and would remain in the race, saying only "Almighty God" could pull him out. An insider who has worked with Mr. Biden for a long time said that signs of aging had become apparent over the past year, but that Mr. Biden's team had failed to address it. Biden's televised debate performance heightened concerns about an already slow-moving issue. Mr. Biden's advisers have long dodged questions about his age. But now they acknowledge that Biden's aging is an undeniable fact. The debate forced the president to more openly acknowledge the limitations of his age, which he had previously largely dismissed. But they have only taken superficial measures and have not fundamentally solved the problem. They replaced the long staircase that Mr. Biden used to board Air Force One with a shorter one; Assistants often accompanied him in public to make his stiff gait less noticeable; While he has a busy schedule, aides have arranged for buffer time, such as long weekends at his homes in Wilmington and Rehoboth Beach, Delaware, or extended stays at Camp David, a Maryland resort, to rest after a "grueling" stretch of travel. Under the authority of one of his top advisers, Anita Dunn, Mr. Biden's public interactions -- especially with reporters -- were severely limited. Even at major events with Democrats or other supporters, the White House sometimes limits the amount of time Biden can spend with the audience, two people familiar with the matter said. As a protective response, designed to protect their longtime boss.





